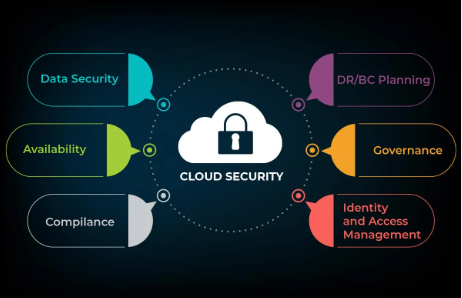
Cloud data security refers to the practices, policies, and technologies designed to protect data stored in cloud computing environments from unauthorized access, breaches, theft, or other forms of cyberattacks. Since organizations increasingly rely on cloud storage and services for data management, ensuring data security in the cloud is critical. Here are key aspects of cloud data security:
1. Data Encryption
- Encryption at Rest: Protecting data while it is stored on the cloud provider’s servers.
- Encryption in Transit: Ensuring data is encrypted while being transmitted between the cloud and users or applications.
- Key Management: Proper management of encryption keys, ensuring they are not compromised or misused.
2. Access Control
- Identity and Access Management (IAM): Using IAM tools to ensure that only authorized users and devices can access data.
- Multi-Factor Authentication (MFA): Adding an additional layer of security by requiring users to provide more than just a password.
- Role-Based Access Control (RBAC): Assigning permissions based on users’ roles, limiting access to sensitive data based on job responsibilities.
3. Data Backup and Recovery
- Automated Backups: Regularly backing up data to avoid loss in case of cyberattacks, data corruption, or natural disasters.
- Disaster Recovery (DR): Ensuring there is a process to recover data and services in case of an outage or breach.
4. Monitoring and Logging
- Real-Time Monitoring: Continuously monitoring cloud environments for unusual activities that might indicate a security threat.
- Audit Logs: Keeping detailed logs of who accessed what data, when, and how, to detect and investigate any potential security issues.
5. Compliance and Legal Considerations
- Regulatory Compliance: Ensuring that the cloud environment adheres to legal and industry-specific regulations (e.g., GDPR, HIPAA, SOC 2, etc.).
- Data Residency: Understanding where your data is physically stored (geographically) and how it is protected by the laws of that jurisdiction.
6. Data Loss Prevention (DLP)
- Preventing Data Exfiltration: Monitoring for unauthorized attempts to transfer sensitive data out of the cloud environment.
- Data Masking and Tokenization: Obscuring sensitive data so that even if it is accessed, it remains unreadable.
7. Shared Responsibility Model
- Provider vs. Customer Responsibilities: Cloud providers typically secure the infrastructure, while customers are responsible for securing the data and managing access. Understanding these responsibilities is vital to maintaining security.
8. Threat Detection and Response
- Security Information and Event Management (SIEM): Aggregating security data from multiple sources to detect and respond to threats quickly.
- AI and Machine Learning: Using advanced technologies to identify patterns of potential attacks and automate threat response.
9. Vendor Security
- Cloud Provider Security: Ensuring the chosen cloud provider follows best security practices, such as offering robust encryption, reliable authentication methods, and ensuring physical security of their data centers.
- Third-Party Integrations: Ensuring that third-party tools or software integrated with the cloud service are secure.
10. Endpoint Security
- Securing Devices: Ensuring that all devices accessing the cloud are secured with up-to-date security software to prevent malware or unauthorized access from compromised endpoints.
11. Zero Trust Architecture
- Adopting a “Zero Trust” model where no device, user, or network is inherently trusted, and every request for access is verified before being granted, regardless of the source.
By addressing these areas, organizations can help protect their cloud-based data from various security threats, ensuring that sensitive information remains confidential and secure.